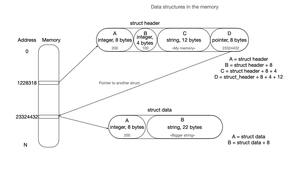
Augmented Tree Data Structures
Data structures are a serious tool to store data conveniently. Modern applications have the flexibility to...

Court Reveals Wright's 2024 MYOB Email Was Manipulated to Support False Claims
Dr. Wright's MYOB Ontier email, supposedly from December 2019, was forged on 18 February 2024. The...

Debunking Craig Wright's Sartre Message
In May 2016, Dr. Craig Wright tried to prove he was Satoshi Nakamoto using the "Sartre...

Holodeck Heroes: Building AI Companions for the Final Frontier
This article is the third in the series of future technology articles—this one focusing on Large...

COPA takes Craig Wright to Court for Impersonating Satoshi Nakamoto with Forged Emails
COPA alleges Dr. Craig Wright forged a January 2014 email from "Satoshi Nakamoto" to support his...
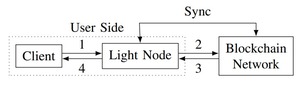
Light Nodes: Balancing Cost and Data Integrity in Blockchain Accessibility
Light nodes offer a cost-effective way to access blockchain data by synchronizing only limited information (like...

Balancing Blockchain Access: Local Nodes vs. Third-Party Services
The choice between running a local full node and relying on third-party services for blockchain access...
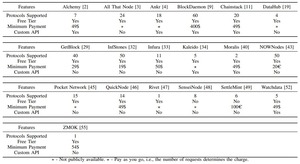
Navigating the Node-as-a-Service Market: Benefits, Risks, and Open Questions
Node-as-a-Service (NAAS) offers a cost-effective alternative to running a full node by outsourcing blockchain access to...
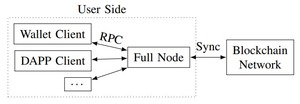
Running a Full Node: A Comprehensive Guide to Maintaining a Blockchain Ledger Locally
Running a full node is a secure method for accessing blockchain information locally, involving direct interaction...

Key Expectations for Blockchain Accessibility: Integrity, Availability, and Privacy
This section discusses the expectations for blockchain accessibility, focusing on integrity, availability, and privacy. It highlights...
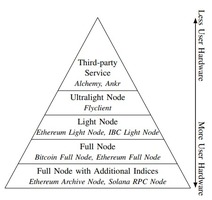
Last Mile of Blockchains: RPC and Node-as-a-Service
The paper compares different methods for accessing blockchains, highlightingthe trade-offs between running a full node and...

Forensic Analysis Exposes Flaws in Craig Wright's Tulip Trust Deed
COPA alleges Dr. Craig Wright forged the Tulip Trust Deed by backdating it to 23 October...

Discovering the Capabilities of IoTeX's Pebble Tracker
The Pebble Tracker by IoTeX is a blockchain-powered IoT device that captures real-time data on location,...

24-Hour vs Detailed Project Development Estimation
24-hour estimation is often opposed to another type of estimation that we call “detailed estimation” for...

Data Engineering: What’s the Value of API Security in the Generative AI Era?
API security is crucial in the era of Generative AI, ensuring data integrity, protecting user privacy,...

What Content to Create and How to Publish It: Part 1
Mastering the Art of Publication: A comprehensive guide outlining key criteria for evaluating publications, common recommendations...

Can Tether Pump BTC Through Uncontrolled Emission?
A years-long lawsuit against Tether and Bitfinex was brought back to life by filing an amended...

Inconsistencies Found in Craig Wright’s MYOB Bitcoin Transactions
COPA alleges that Dr. Craig Wright forged MYOB accounting records to backdate Bitcoin transactions, supporting his...
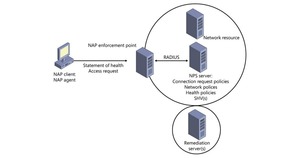
Network++ Part 2
NAS refer to service s allow user to access computer networks or the internet. These services...

The Importance Of a Routine Smart Contract Audit In Blockchain Security
Smart contracts are pieces of self-executing computer programs on a blockchain. They are designed to function...

How I Implemented Access Approval in Our Open Source Project
Makaut Buddy, a notes-sharing platform for university students, faced challenges in managing user uploads securely. This...

RGB++ Layer: Transforming Bitcoin with Asset Issuance, Smart Contracts, and Interoperability
RGB++ Layer is an upgraded concept from the __[RGB++ protocol. It extends isomorphic binding, smart contract...

Hex-Edited Bitcoin Executable Linked to COPA's Forgery Claims
Dr. Craig Wright's bitcoin.exe document, purportedly from January 2009, is alleged to be a forgery by...
COPA Accuses Craig Wright of Manipulating Bitcoin Flowchart Documents
A document claimed by Dr. Wright to be an early Bitcoin source code flowchart is alleged...

C++ Code Documents in Bitcoin Case Deemed Forgery
Two C++ source code documents claimed to be early Bitcoin models by Dr. Wright are alleged...

Crypto Open Patent Alliance Finds Evidence of Tampering in Wright's Claim to be Bitcoin Founder
A document dated December 2008, purported to be a precursor to the Bitcoin White Paper, is...

How to Detect and Minimise Hallucinations in AI Models
While it is evident that machine learning algorithms are able to solve more challenging requirements, they...

How Bitcoin Merges Religion, Philosophy, and Innovation to Unlock Financial Prosperity
We are answering a few questions as follows: What is Bitcoin? Bitcoin is a programmable money,...

Binary Size in Go Applications: How to Use Go-size-analyze
Go is known for its simplicity and efficiency, but as projects grow in size, so can...

Advancements in Bitcoin Scaling — Side Chains and Layer 2 Solutions as Key Players
Detailing Bitcoin’s journey in scaling, the role of Layer 2 solutions and Side Chains and prospects...

10 LeetCode Patterns to Solve 1000 LeetCode Problems
10 LeetCode Patterns that solve 1000 LeetCode Problems. Too optimistic? Not at all. These 10 patterns...

How to Build a Request Access Approval System Using Next.js
Next.js is a powerful React framework for creating fast, scalable web applications with server-side rendering and...

Using AI to Combat Counterfeit Goods in the Supply Chain
It's relatively easy to slip counterfeit goods into the supply chain, damaging economies, companies, and individuals....

How to Improve Your Workflow by 10X: 17 Essential Apps
I've curated a list of 17 top-tier tools from graphic editor suites and wireframing tools to...

How to Debug and Solve a Big Production Problem With SaaS
In this article I outline a comprehensive guide for software engineers and related roles on how...

Balance Is Killing Your Ambition: How to Become World Class
Everything the best athletes do is to improve their game performance. If you play several distracting...
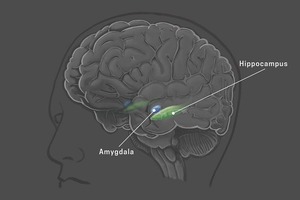
Particle Physics Neuroscience: Does e = mc^2 Have an Equivalent for the Human Mind?
It is theorized that in a set, electrical signals strike to fuse briefly with chemical signals,...

The Top 5 Angular DataGrids
Learn about the Top 5 Angular DataGrids for your web applications and their notable features in...

Why C-Suite Executives Won’t Cut it Without Data Skills Anymore
Every industry generates massive amounts of data, which is now being used for better decision-making. One...

Building a Simple Custom Processor With Apache Ni-Fi
Apache NiFi is a powerful tool for automating data flows with a large number of built-in...
From Outputs to Outcomes
Shifting from output to outcome can be stressful but rewarding. Empower your Scrum teams with guidance,...
Our Short-form Series Perform Better Than Netflix. Here's How we Film Them
Explore how vertical short-form video series are disrupting traditional streaming, with insights on creating mobile-first content...

Morpheus.Network: Changing the Face of Global Supply Chains
Founded in 2017, Morpheus.Network, a Toronto-based company, has harnessed blockchain technology to address the complex challenges...
Custom Built vs Off-the-Shelf Apps: 8 Things You Need to Know Before Making a Decision
Contrasting custom and COTS software solutions for businesses by reviewing eight essential points of comparison.









