~hackernoon | Bookmarks (1975)
-
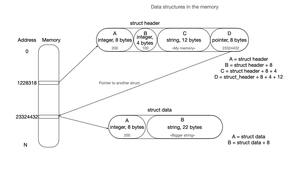
Augmented Tree Data Structures
Data structures are a serious tool to store data conveniently. Modern applications have the flexibility to...
-
Court Reveals Wright's 2024 MYOB Email Was Manipulated to Support False Claims
Dr. Wright's MYOB Ontier email, supposedly from December 2019, was forged on 18 February 2024. The...
-
Debunking Craig Wright's Sartre Message
In May 2016, Dr. Craig Wright tried to prove he was Satoshi Nakamoto using the "Sartre...
-
Holodeck Heroes: Building AI Companions for the Final Frontier
This article is the third in the series of future technology articles—this one focusing on Large...
-
COPA takes Craig Wright to Court for Impersonating Satoshi Nakamoto with Forged Emails
COPA alleges Dr. Craig Wright forged a January 2014 email from "Satoshi Nakamoto" to support his...
-
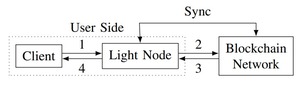
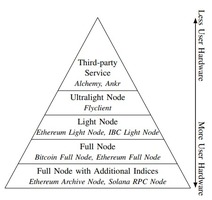
Light Nodes: Balancing Cost and Data Integrity in Blockchain Accessibility
Light nodes offer a cost-effective way to access blockchain data by synchronizing only limited information (like...
-
Balancing Blockchain Access: Local Nodes vs. Third-Party Services
The choice between running a local full node and relying on third-party services for blockchain access...
-
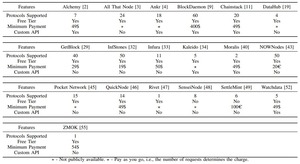
Navigating the Node-as-a-Service Market: Benefits, Risks, and Open Questions
Node-as-a-Service (NAAS) offers a cost-effective alternative to running a full node by outsourcing blockchain access to...
-
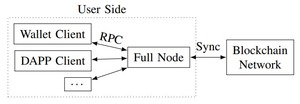
Running a Full Node: A Comprehensive Guide to Maintaining a Blockchain Ledger Locally
Running a full node is a secure method for accessing blockchain information locally, involving direct interaction...
-
Key Expectations for Blockchain Accessibility: Integrity, Availability, and Privacy
This section discusses the expectations for blockchain accessibility, focusing on integrity, availability, and privacy. It highlights...
-
Last Mile of Blockchains: RPC and Node-as-a-Service
The paper compares different methods for accessing blockchains, highlightingthe trade-offs between running a full node and...
-
Forensic Analysis Exposes Flaws in Craig Wright's Tulip Trust Deed
COPA alleges Dr. Craig Wright forged the Tulip Trust Deed by backdating it to 23 October...
-
Discovering the Capabilities of IoTeX's Pebble Tracker
The Pebble Tracker by IoTeX is a blockchain-powered IoT device that captures real-time data on location,...
-
24-Hour vs Detailed Project Development Estimation
24-hour estimation is often opposed to another type of estimation that we call “detailed estimation” for...
-
Data Engineering: What’s the Value of API Security in the Generative AI Era?
API security is crucial in the era of Generative AI, ensuring data integrity, protecting user privacy,...
-
What Content to Create and How to Publish It: Part 1
Mastering the Art of Publication: A comprehensive guide outlining key criteria for evaluating publications, common recommendations...
-
Can Tether Pump BTC Through Uncontrolled Emission?
A years-long lawsuit against Tether and Bitfinex was brought back to life by filing an amended...
-
Inconsistencies Found in Craig Wright’s MYOB Bitcoin Transactions
COPA alleges that Dr. Craig Wright forged MYOB accounting records to backdate Bitcoin transactions, supporting his...
-
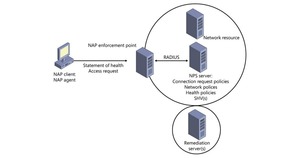
Network++ Part 2
NAS refer to service s allow user to access computer networks or the internet. These services...
-
The Importance Of a Routine Smart Contract Audit In Blockchain Security
Smart contracts are pieces of self-executing computer programs on a blockchain. They are designed to function...
-
How I Implemented Access Approval in Our Open Source Project
Makaut Buddy, a notes-sharing platform for university students, faced challenges in managing user uploads securely. This...
-
RGB++ Layer: Transforming Bitcoin with Asset Issuance, Smart Contracts, and Interoperability
RGB++ Layer is an upgraded concept from the __[RGB++ protocol. It extends isomorphic binding, smart contract...
-
Hex-Edited Bitcoin Executable Linked to COPA's Forgery Claims
Dr. Craig Wright's bitcoin.exe document, purportedly from January 2009, is alleged to be a forgery by...
-
COPA Accuses Craig Wright of Manipulating Bitcoin Flowchart Documents
A document claimed by Dr. Wright to be an early Bitcoin source code flowchart is alleged...